ConSol CM offers LDAP authentication for the Web Client as a standard feature, i.e., instead of managing the passwords for the ConSol CM engineers in the ConSol CM database, they can be retrieved from an LDAP server (like e.g., a Microsoft Active Directory server).
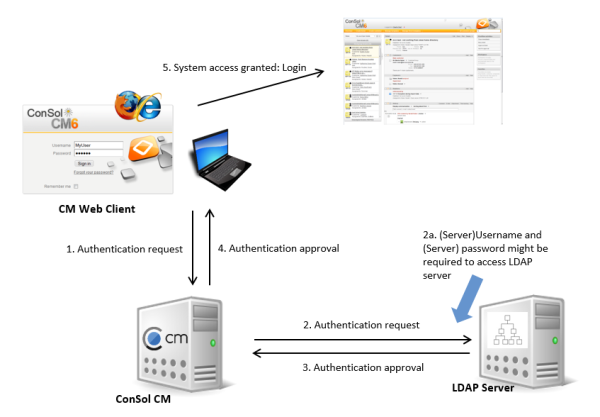
When engineers want to log in to the ConSol CM Web Client, they enter their user name and password and press Enter. Behind the scenes, the ConSol CM server sends a request with the engineer's user name and password and asks the LDAP server whether those credentials are correct.
If the credentials are correct, the approval is sent back to the ConSol CM server and the engineer is logged into the Web Client.
Please keep in mind that the LDAP connection is only used to authenticate the user (confirm the identity). The authorization (i.e., the assignment of access permissions in the system) is done via the engineer and role administration in the Admin Tool. For every user who should work with the system as an engineer, an engineer account has to be created in the engineer administration!
Please see also the following picture for an explanation of the CM authentication process using LDAP.
Figure 478: ConSol CM - LDAP authentication process
There are two ways you can enable the ConSol CM system to use LDAP authentication:
During system set-up you can select LDAP as the authentication mode. This will set the system property cmas-core-security, authentication.method (see below) to LDAP. No further parameters are entered. You have to set the LDAP parameters manually. Please see the next section for an explanation.
Figure 479: ConSol CM system set-up - Authentication mode LDAP
Figure 480: ConSol CM Admin Tool - System properties for LDAP authentication
Required values for LDAP authentication (they are set via system properties, please see System Properties for an explanation):
ldap.userdn
LDAP user for connecting to the LDAP server to look up users. Only needed if look-up cannot be done anonymously.
A server user name/password pair might be required to access the LDAP server. If you are not sure, you might want to use an LDAP browser to confirm.
ldap.providerurl
The complete URL for the LDAP server:
ldap://<HOSTNAME>:<LDAP PORT>
Use the Engineer Administration in the Admin Tool to configure the engineer accounts.
When LDAP is used as authentication method, it is not possible to set the ConSol CM password within the engineer administration. The pop-up window for engineer management provides the following fields which are relevant for LDAP authentication. Please refer to section Engineer Administration for details concerning the other (non LDAP-related) data fields.
Figure 481: ConSol CM Admin Tool - Engineer administration
Per default, when an LDAP client accesses an LDAP server, the information is transferred in clear text. In case you want the user name and password to be transferred to the LDAP server in encrypted form, you have to set up the LDAP authentication using LDAPS.
You have to configure the CM server machine (Java) in a way that can use certificates. One way to do this for a Linux environment is described in the following section.
openssl s_client -connect dc2.mydomain.com:ldaps$JAVA_HOME/bin/keytool -import -alias <arbitrary> -trustcacerts
-keystore /home/mydirectory/mytruststore
-file/tmp/certificate2_dc2_mydomain_com.txt-Djavax.net.ssl.trustStore=/home/mydirectory/mytruststore
-Djavax.net.ssl.trustStorePassword=<see above>Configure the ConSol CM server as shown in the following example:
Depending on the LDAP server configuration, use one of the following values for the server URL: