LDAP Authentication for Customers in CM/Track
Introduction to ConSol CM LDAP Authentication
ConSol CM offers LDAP authentication for CM/Track as a standard feature, i.e., instead of managing the passwords for the ConSol CM customers in the ConSol CM database, they can be retrieved from an LDAP server (like e.g., a Microsoft Active Directory server).
When customers want to log in to CM/Track, they enter their user name and password and press Enter. Behind the scenes, the ConSol CM server sends a request with the customer's user name and password and asks the LDAP server whether those credentials are correct.
If the credentials are correct, the approval is sent back to the ConSol CM server and the customer is logged into CM/Track.
Please keep in mind that the LDAP connection is only used to authenticate the customer (confirm the identity). The authorization (i.e., the assignment of access permissions in the system) is done via the assignment of a CM/Track user profile in the Web Client. The CM/Track user profiles are managed in the engineer and role administration in the Admin Tool.
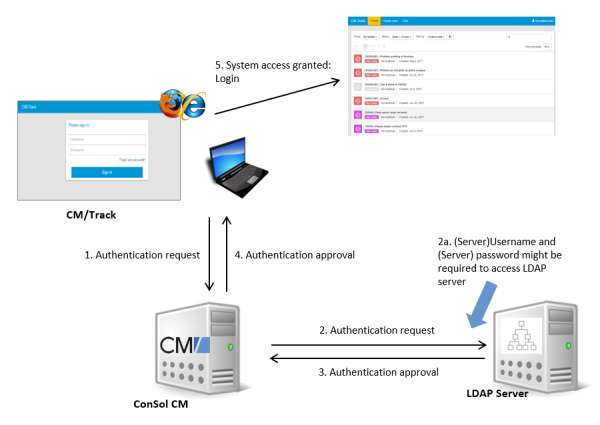
Please see also the following picture for an explanation of the CM/Track authentication process using LDAP.
Figure 437: ConSol CM - LDAP authentication process for CM/Track
Configuring LDAP Authentication
LDAP authentication is activated by setting the system property cmas-core-security, contact.authentication.method to LDAP.
Then you have to set the required values in the system properties (navigation group System, navigation item System Properties
The LDAP servers can be defined using the following system properties from the module cmas-core-security.
{name} is a string that you can choose to distinguish LDAP servers. It must always be set, even if only one LDAP server is configured. You should use a simple string for the {name}, not containing any keywords, like internal or external, and which does not contain special characters.
- cmas-core-security, contact.authentication.method
LDAP - ldap.contact.{name}.providerurl
The property value is the address of the LDAP server in the form ldap[s]://host:port. - ldap.contact.{name}.userdn
The value is the user DN used to look up the contact DN by the LDAP ID. An anonymous account is used if the value is not set. - ldap.contact.{name}.password
The property contains the password to look up the contact DN by the LDAP ID. An anonymous account is used if the value is not set. - ldap.contact.{name}.basedn
This represents the base path to search for the contact DN by the LDAP ID, e.g., ou=accounts,dc=mycompany,dc=de. - ldap.contact.{name}.searchattr
The property value stands for the attribute to search for the contact DN by the LDAP ID, e.g., uid.
Initially, these system properties might not be present in your CM system. Just add them manually. Changes to any of the above system properties do not require a server restart and are propagated to all cluster nodes. The use of the placeholder {name} allows configurations to define several different LDAP servers.
- ldap.initialcontextfactory
This is a predefined global property. If it is not set, com.sun.jndi.ldap.LdapCtxFactory is used as its value.
Authentication attempts against LDAP servers are made until first success, where the server order is determined by their {name} values (ascending alphabetical order of the values).
Mixed Authentication Mode
Set the system property cmas-core-security, contact.authentication.method depending on the desired order of authentication instances:
- LDAP,DATABASE:
First attempt authentication using the available LDAP server(s), if an LDAP ID is provided. On failure, try a database login if the customer has a database password. - DATABASE,LDAP:
First attempt a database login if the customer has a database password. On failure try authentication using the available LDAP server(s) if an LDAP ID is provided.
The CM system will first contact the instance which is mentioned first, than the second one. For example, when the contact authentication method is set to LDAP,DATABASE and the customer (contact) uses the password which is only valid in the database, the login will succeed.
In server.log the following message will be displayed:
LDAP login failed: [LDAP: error code 49 - Invalid Credentials]; nested exception is javax.naming.AuthenticationException: [LDAP: error code 49 - Invalid Credentials]
Logging of LDAP Login Attempts in CM/Track
All LDAP errors encountered are logged without a stack trace using loggers with the following prefix:
- com.consol.cmas.core.security.contact
The stack trace of LDAP errors is not logged because failed login attempts on the first LDAP server would clutter logs if a following login on the second LDAP server succeeded.
Using LDAPS (LDAP over SSL)
Introduction
Per default, when an LDAP client accesses an LDAP server, the information is transferred in clear text. In case you want the user name and password to be transferred to the LDAP server in encrypted form, you have to set up the LDAP authentication using LDAPS.
Preparations
You have to configure the CM server machine (Java) in a way that can use certificates. One way to do this for a Linux environment is described in the following section.
-
Retrieve the certificate:
openssl s_client -connect dc2.mydomain.com:ldaps
-
The answer will contain a section which starts with "---BEGIN CERTIFICATE " and ends with "END CERTIFICATE ---". Copy this section to a file, e.g., /tmp/certificate2_dc2_mydomain_com.txt
-
Import the certificate to the truststore of your machine, e.g., /home/mydirectory/mytruststore
$JAVA_HOME/bin/keytool -import -alias <arbitrary> -trustcacerts -keystore /home/mydirectory/mytruststore -file/tmp/certificate2_dc2_mydomain_com.txt
You have to enter (set) a password.
-
Enter the truststore in the ConSol CM config file in JAVA_OPTS:
-Djavax.net.ssl.trustStore=/home/mydirectory/mytruststore -Djavax.net.ssl.trustStorePassword=<see above>
LDAPS Configuration in the ConSol CM Admin Tool (System Properties)
Configure the ConSol CM server as shown in the following example:
- cmas-core-security, ldap.authentication = simple
- cmas-core-security, ldap.contact.name.basedn = OU=myOU,DC=myDC
- cmas-core-security, ldap.initialcontextfactory = com.sun.jndi.ldap.LdapCtxFactory
- cmas-core-security, ldap.contact.name.password = myLDAPpw
- cmas-core-security, ldap.contact.name.searchattr= sAMAccountName
- cmas-core-security, ldap.contact.name.userdn = myLDAP_UserDN
Depending on the LDAP server configuration, use one of the following values for the server URL:
- Standard LDAPs port
cmas-core-security, ldap.contact.name.providerurl = ldaps://dc2.mydomain.com:636 - LDAPs port Global Catalogue
cmas-core-security, ldap.contact.name.providerurl = ldaps://dc2.mydomain.com:3269
Setting Up Customer Accounts for LDAP
There are two steps which you need to perform to set up LDAP authentication for customers using CM/Track:
- Set the required annotation for the customer field which should hold the LDAP ID in the Admin Tool.
- Enter the LDAP IDs for the actual customers in the Web Client.
When LDAP mode is used, the customer field which is used for the CM/Track user name (login) has to have two annotations: