Operating ConSol CM behind a proxy (e.g., Apache HTTPD)
Introduction
In some cases, it might be required to operate ConSol CM behind a proxy server. Two common scenarios are:
- The Web Client and CM/Track should be available through the proxy, but external access through the proxy to the Admin Tool and to the Process Designer should be blocked. This is explained in section ConSol CM behind a proxy, blocking Admin Tool and Process Designer.
- All clients, i.e. Web Client, CM/Track, Admin Tool, and Process Designer should be available through the proxy. This is explained in section ConSol CM behind a proxy, allowing access to Admin Tool and Process Designer.
ConSol CM behind a proxy, blocking Admin Tool and Process Designer
Basic principle
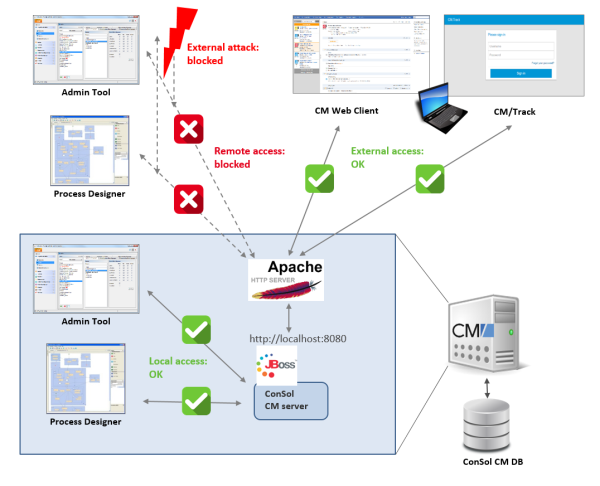
This section provides information about how to operate ConSol CM behind a proxy server (e.g. Microsoft IIS or Apache HTTPD). This might be relevant in a security context, e.g. when you have to set security regulations concerning system access over the internet. You might have to
grant access
- for your engineers to the Web Client (URL http://<yourcm6server>/cm-client)
- for your customers to CM/Track (URL http://<yourcm6server>/restapi) and if CM/Track is deployed in the CM JBoss also URL http://<yourcm6server>/track)
but to
block access
- to the Admin Tool and
- to the Process Designer.
The solution is based on the principle shown in the following picture.
Figure 19: Operating ConSol CM behind a proxy server (here Apache HTTP server)
Hide some CM URLs behind an Apache proxy server (= whitelist only dedicated applications)
This section demonstrates how to allow only certain URLs / paths / applications to be accessible through the proxy. This will hide all other addresses.
The solution is based on an Apache HTTPD version 2.4 and assumes:
- that the JBoss bind address (-b parameter) has been set to 127.0.0.1 so it will only allow connections from the local machine
- that the Apache HTTPD and the JBoss reside on the same machine (applicable for most CM installations except for clustered environments)
Perform the following steps:
- Install the Apache HTTP server
- Activate the proxy modules
- Add the proxy rules
- Test your installation
Install the Apache HTTP server
Since Windows binaries (ZIP archive with EXE files) are not directly available on the Apache homepage, we recommend to download the binary files from the Apache Haus.
Activate the proxy modules
In <APACHE_HOME>/conf/httpd.conf you need to un-comment the following proxy modules to activate proxy functionality:
LoadModule proxy_module modules/mod_proxy.so
LoadModule rewrite_module modules/mod_rewrite.so
LoadModule proxy_ajp_module modules/mod_proxy_ajp.so
# LoadModule proxy_http_module modules/mod_proxy_http.so # if you want to use http backend
Add the proxy rules
Add the following section at the end of the <APACHE_HOME>/conf/httpd.conf file.
Best practice is to use AJP as a backend protocol.
<IfModule proxy_ajp_module>
ProxyPass /cm-client ajp://localhost:8009/cm-client disablereuse=on
ProxyPassReverse /cm-client ajp://localhost:8009/cm-client
ProxyPass /restapi ajp://localhost:8009/restapi disablereuse=on
ProxyPassReverse /restapi ajp://localhost:8009/restapi
# If CM/Track is deployed on the JBoss directly, you might want to enable the following lines as well
ProxyPass /track ajp://localhost:8009/track disablereuse=on
ProxyPassReverse /track ajp://localhost:8009/track
</IfModule>
Set disablereuse=on to force mod_proxy to close connections to its backend after using it. Otherwise you could get issues with things being loaded with delay or not loaded at all, especially in situations with a firewall between Apache and JBoss.
Alternative with rewrite rules to allow easier access using http://<yourcm6server>/. The following lines have to be added to the <VirtualHost *:443> section of the configuration:
RewriteEngine on
RewriteRule ^/$ /cm-client/ [R,L]
RewriteRule ^/cm-client$ /cm-client/ [R,L]
ProxyPass /cm-client/ ajp://localhost:8009/cm-client/ disablereuse=on
ProxyPassReverse /cm-client ajp://localhost:8009/cm-client
RequestHeader set X-Forwarded-Proto "https"
If you use the notifications feature, you also need to add the following lines:
ProxyPass /atmosphere/ ws://localhost:8009/atmosphere/
ProxyPassReverse /atmosphere/ ws://localhost:8009/atmosphere/
Test your installation
Client test
Once these modifications are complete, start the httpd (e.g.: execute httpd.exe located in the bin/ directory) and start the CM JBoss.
Now you should be able to access:
http://<yourcm6server>/cm-client/login
which should display the regular ConSol CM login page.
Figure 20: ConSol CM login page
Accessing
http://<yourcm6server>/admin/cm-admin-tool.jnlp
should just result in a HTTP 404 (Page not found).
REST API test
Basically do the same to test the proxy rule for the ConSol CM REST API.
http://localhost/restapi/echo/client
This call should display some JSON string:
{"Accept-Language":"de,en-US;q=0.7,en;q=0.3","Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,*/* ;q=0.8"}
Installing Apache HTTPD as a Windows service
On Windows machines, you might want to run the Apache HTTPD as a service.
The following command needs to be run with administrator permissions in order to install the Apache HTTPD as a Windows service:
D:\work\Apache24\bin>httpd.exe -k install
It will result in the following output:
Installing the 'Apache2.4' service
The 'Apache2.4' service is successfully installed.
Testing httpd.conf....
Errors reported here must be corrected before the service can be started.
D:\work\Apache24\bin>
Please make sure that the start mode of this service is automatic (same as the JBoss service).
ConSol CM behind a proxy, allowing access to Admin Tool and Process Designer
Configuring AJP support for JBoss EAP
In case you want to operate ConSol CM behind a proxy server and want to explicitly allow access to the Admin Tool and to the Process Designer, you have to enable AJP in the JBoss installation.
The AJP connector is enabled by default in the ConSol CM configuration file (cm6-<DB>.xml). The respective entry looks as follows:
<ajp-listener name="ajp" socket-binding="ajp"/>
By default, AJP uses port 8009. In order to change this port, add the variable jboss.socket.binding.ajp.port to your configuration file, e.g. cm6-config.properties, and specify the desired port:
# port overrides
jboss.socket.binding.ajp.port=8009