Email Encryption
Introduction
Due to security policies, it might be required to encrypt email traffic (including the emails which are sent and received by the ConSol CM installation) using standard S/MIME encryption. If the topic is new to you, you might want to read some articles about it, e.g. the Public-key cryptography article in Wikipedia.
In order to enable the use of encrypted emails with ConSol CM, you first have to enable the email encryption in the system:
- Mandatory:
Set the system property cmas-core-server, mail.encryption to true. It is set to false as default value. This is the basic configuration to enable email encryption for the entire system. - Optional:
Set the page customization attribute mailEncryptionAvailable to true. This activates an option in the Web Client to choose whether an email should be encrypted.
General Explanation about Email Encryption in ConSol CM
There are two types of certificates:
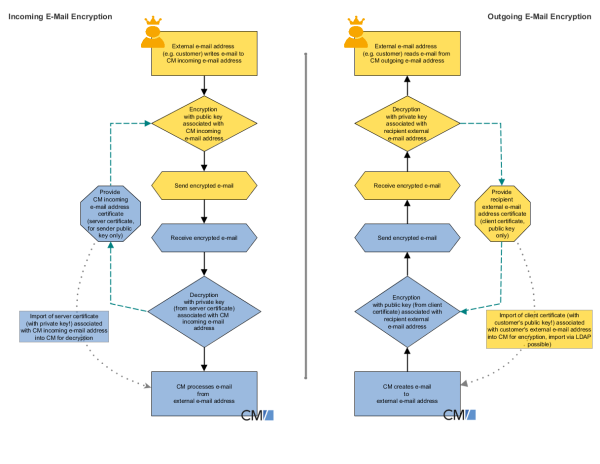
- Server certificates, mainly used for incoming emails
The public key (in the certificate) and the private key of the receiving email address can be manually imported into the CM system from a PKCS12 file (.p12 or .pfx). If the certificate is password-protected, the administrator has to provide this password when the certificate is imported. - Client certificates, used for outgoing emails
For outgoing emails, the certificates (public keys) of the receiving email addresses are required. These certificates can be imported into the CM system in two ways:- Manually
By selecting (uploading) the respective X.509 file (.cer or .crt) - Automatically
From an LDAP repository where it is stored in the correct format (i.e. in the same format which is required for the file import). This automatic retrieval of the requested certificate can be performed on-the-fly when the email is sent.
- Manually
The certificates discussed here are used for email encryption only and not for the access of ConSol CM (as email client) to the email server! That has to be managed using certificates which are stored in the security store of the application server.
The following figure shows the basic principle of email encryption for incoming and outgoing emails in ConSol CM.
Figure 388: Basic principle of ConSol CM email encryption
Requirements
- The client certificate must contain the email address of the customer (receiver of the email) in the attribute SubjectDN (E= or EMAILADDRESS=) or the X509v3 Subject Alternative Name element from the Extensions section of the certificate.
- Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files has to be installed on the server and on the machine where the Admin Tool is started. This is required to enable the Admin Tool to import certificates.
- X.509 Base64-encoded certificates are supported.
Certificate Import from LDAP (Available for Client Certificates)
If LDAP is configured, ConSol CM will look up the client certificate for the requested contact in the LDAP repository. This is done as follows:
- Someone tries to send an encrypted email.
- The cryptography service looks for a client certificate (with the public key) of the recipient.
- If a client certificate is found, the email is encrypted using the client's public key and sent.
- If a client certificate is not found in the Admin Tool or it has expired, it is looked up in the LDAP repository.
- If it is found, it is imported to ConSol CM and the email is encrypted and sent.
- If it is not found, the email is sent unencrypted.
The following configuration properties have to be set to enable certificate lookup via LDAP:
Please see section LDAP certificate parameters in System Properties for details.
Certificate Management in the Admin Tool
In the Admin Tool, the navigation items Server Certificates and Client Certificates in the navigation group Email are used to configure the CM environment for email encryption.
Server Certificates
Server certificates are used to decipher incoming email messages. In some exceptional cases, they are also used to encrypt outgoing emails: if one of the recipients is the same as one of the incoming email accounts, the server certificate will be used to encrypt that message. Server certificates each contain the public and the private key for the given email address. If you define an incoming email account (see section above), you have to upload a server certificate for that email address (or for all email addresses covered by this mailbox) to be able to receive encrypted messages (because the server certificate contains the respective private key). If you have several incoming accounts, you either have to upload a server certificate for each of them or you can upload one certificate with all required email addresses.
When you open the navigation item Server certificates, a list of all existing server certificates is displayed. To add a new server certificate, click the Add button and use the file browser to find the required certificate. The certificate is validated before it is imported. If there are any incompatibilities, an error message is displayed and the certificate is not imported.
Supported formats for server certificates are:
- PKCS #12 archive file containing certificate (public) and private key (password protected).
Supported filename extensions for PKCS #12 files are:- .p12
- .pfx
Client Certificates
A client certificate contains only the public key of an external recipient (e.g., a customer). It allows encrypting messages which are sent to that user, i.e. client certificates are used for outgoing emails.
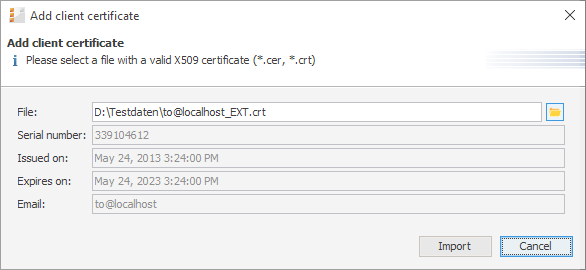
When you open the navigation item Client certificates, a list of all existing client certificates is displayed. To add a new client certificate, click the Add button and use the file browser to find the required certificate. The certificate is validated before it is imported. If there are any incompatibilities, an error message is displayed and the certificate is not imported.
Supported formats for client certificates are:
- X509 standard format.
Supported file name extensions for X.509 certificates are:- .cer
- .crt
- .der
- .pem
Figure 389: ConSol CM Admin Tool - Email, Client Certificates: Pop-up window for adding a client certificate
Here are some example use cases:
- An engineer works in the ConSol CM Web Client and writes an encrypted email using the Ticket Email Editor. When the Send button is clicked, the ConSol CM system looks up the receiver address in the list of email addresses under Client certificates and uses the public key of the recipient to encrypt the outgoing email. If ConSol CM cannot find a matching certificate (the email address is not in the certificate list), the certificate for the email address is loaded from LDAP. If no compatible certificate is found there either, the email is sent unencrypted.
If one of the recipients is one of the incoming email accounts, the server certificate (public key) will also be used to encrypt that message. - ConSol CM receives an email and checks the To address. If it is found in the list under Server certificates, ConSol CM uses the private key given in this certificate to decrypt the message and to either create a new ticket or append the message to an existing ticket.
Sending Encrypted Emails
Choosing if Emails Should Be Sent Encrypted from the Web Client
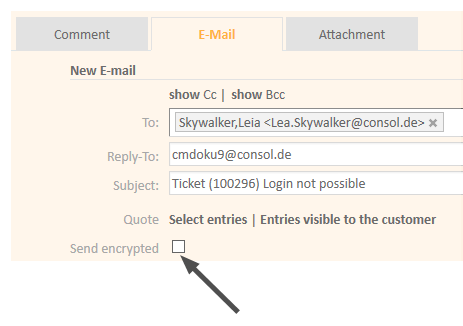
If the page customization property mailEncryptionAvailable has been set to true, a checkbox Send encrypted is available in the Ticket Email Editor in the Web Client. Thus, the user can choose whether the email should be sent encrypted.
Figure 390: ConSol CM Web Client - Send encrypted email
Sending an Encrypted Email from the Workflow
An encrypted email can be sent by using the method enableEncryption(). Please see the ConSol CM Process Designer Manual for a detailed explanation.
Sending Encrypted Emails by Default
If the system property cmas-core-server, mail.encryptionis set to true, all outgoing emails from the workflow and Web Client are encrypted by default.
If users would like to send selected emails unencrypted, they can uncheck the checkbox Send encrypted in the Web Client. For emails sent by the workflow the method disableEncryption() can be used for this purpose.